For a project that has no hope of ever going forward, the folks behind the $36 billion Pacific NorthWest LNG project and associated pipeline sure are spending a lot of money on it.
Petronas’ PNW LNG project certainly has its problems: Low oil prices, an environmentally problematic site, opposition from First Nations, a glacial review process and a new Liberal government that has, so far, demonstrated a lukewarm attitude towards fossil fuels.
I can see why this project has resulted in so many news stories and opinion pieces predicting the project will be stillborn. I’ve had some doubts about it myself.
So why does Petronas and its partners continue to pump so much money into this project, if they’re not serious about moving ahead?
Petronas has already spent billions here in B.C. on acquiring and building out upstream gas assets. And there are signs that the company is still planning to move ahead with it.
As I reported in January, Petronas has leased two floors at the Park Place office tower. Why would they do that if they were taking a wait-and-see attitude?
And just yesterday, Jonny Wakefield at the Alaska Highway News tweeted this out.
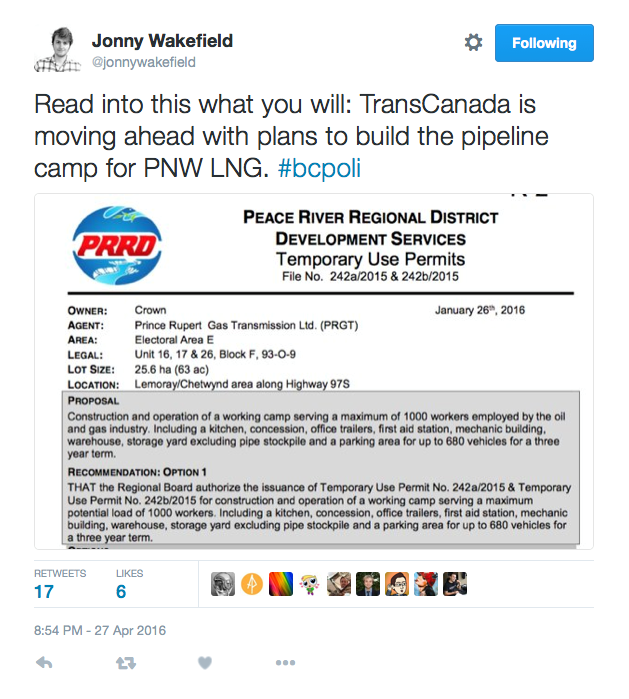
It’s a temporary use permit application with the Peace River Regional District by TransCanada Corp. (TSX:TRP) for a 1,000-person work camp for the construction of the Prince Rupert Gas Transmission line.
This is the pipeline that would take natural gas from the Peace Region to the PNW LNG plant on Lelu Island in Prince Rupert.
The camp would be in the Chetwynd area. As Wakefield points out, this is just one of nine work camps that will be needed for the pipeline construction project.
Every time there is some negative news about this project, it stokes the hopes of those who are opposed to LNG that this project is dead in the water. I think that may be wishful thinking on their part.
Goldcorp hacked
News this week that Goldcorp. Inc. (TSX:G) had been the victim of a hacking attack that may have resulted in a massive release of confidential employee and company information should give every business the jitters.
An Internet news site called dailydot.com broke the story. It managed to confirm the veracity of what hackers had claimed online: that it had obtained a trove of Goldcorp employee and company information – from employee logins and passwords, to banking information and internal emails.
The dailydot.com reported that the hackers were planning to release the information:
“[S]everal more data dumps are being prepared. [T]he next dump will include 14 months of company wide emails, emails containing some good old fashion corporate racism, sexism, and greed.”
It is the second time a Canadian gold mining company has been hacked in recent months.
In a number of corporate hacking cases, there are strong suspicions that state actors may be involved – Russia and China, for example. I have a sneaking suspicion Vladimir Putin isn’t behind this one.
This is just a hunch, but I’m thinking it could be some geeky social justice hacktivist who hacked Goldcorp just because he could.
I picture a slightly overweight 25-year-old virgin with Fritos cheese smears on his No Logo T-shirt, hunkered over a keyboard in his mom’s basement overdosing on Red Bull and self righteousness.
Still, isn’t that a frightening idea? That some loser with nothing but a computer and time on his hands can cost a company like Samsung or Goldcorp a fortune in damage control?
Dale Jackaman, president of Amuleta Computer Security Inc., which specializes in cyber crime, computer security and industrial espionage, tells me: "Most companies just don't get it on the IT security side and hacking exploits like this are common place.
“The real cost of this kind of exploit will be orders of magnitude more expensive that what it would have cost to properly secure the company in the first place.”
That may sound a bit like blaming the victim, like when you get mugged in a dark alley and police suggest you shouldn’t be walking down a dark alley at night.
Obviously companies need to take the IT security seriously, but I think its time governments and police forces also took it more seriously as well with tougher penalties and more IT security resources.




